Security measures to take when outsourcing IT services
Don’t worry, take control!
Outsourcing IT infrastructure services is a logical step for a growing business. When a qualified contractor is selected, it allows an organization to optimize IT costs and improve quality of service. IT outsourcing also creates the flexibility to regulate the volume of services delivered. If a company’s needs change rapidly, contractors can promptly ramp up or down the volume of IT services.
IT outsourcing requires that a company review its organizational processes to properly establish cooperation with IT service providers. In addition, the company should consider the risks associated with transferring infrastructure control (network and server administration, all key account data, etc) to a third-party provider and its employees. In other words, the company provides a significant management leverage over their business to an outside company, which can never be 100% reliable.
So how do you minimize the risks? This issue has been explored more extensively than you might expect at first glance. To minimize potential risks, you can use organizational and technical control measures.
Organizational measures include the creation of an «IT Government» unit within the organization – a sort of «government» along with its competencies, such as coordinating and supervising contractors, and influencing their actions, including limiting their access or blocking them.
Available technical measures include software and hardware products that provide accurate control over outsourced IT employees by auditing and recording all actions performed by a remote administrator.
Below is a list of the industry’s most popular products, along with URLs so you can evaluate these solutions yourself:
| Company | Website | Products |
|---|---|---|
| TSFactory (USA) | https://www.tsfactory.com/ | RecordTS – terminal session audit and recording (Terminal Services, Citrix, vWorkSpace) |
| ObserveIT (USA-Israel) | http://www.observeit.com/ | Visual session recording – audit, alerting and user session recording on Windows and Unix servers. |
| СensorNET (UK-USA) | https://www.censornet.com/ | Desktop Monitoring – online monitoring, audit and recording user actions. |
| BalaBit (USA-Hungary) | https://www.balabit.com/ | Shell Control Box – software and hardware complex for control, audit and recording remote sessions. |
BalaBit Shell Control Box as a possible solution
Let us take a closer look at what we believe is the most interesting solution, BalaBit Shell Control Box.
Shell Control Box (SCB) stands out from the crowd, because it is not just a set of agents for client and server machines. It is an independent device that controls, monitors and audits remote administrators’ access to servers, providing full transparency and independence from clients and servers.
SCB is a tool for supervising server administrators and administration processes by managing the encrypted connections used in server administration. SCB fully controls connections made via SSH, RDP, Telnet, TN3270, Citrix ICA and VNC, creating a clear set of functions and a controlled access level for administrators.
Among SCB’s most significant features are the following:
- Ability to disable unwanted channels and features (for example, TCP port redirection, file transfer, VPN, etc.);
- Control over selected authentication methods;
- Required external authentication on the SCB gateway;
- Implementation of authorization with the ability to monitor and audit in real time;
- Encrypted auditing of selected channels; time-tagged and digitally signed audit trails;
- Information about user group membership through the LDAP database;
- Keys and server host certificates with SCB access can be checked, configured, and managed using any modern web browser.
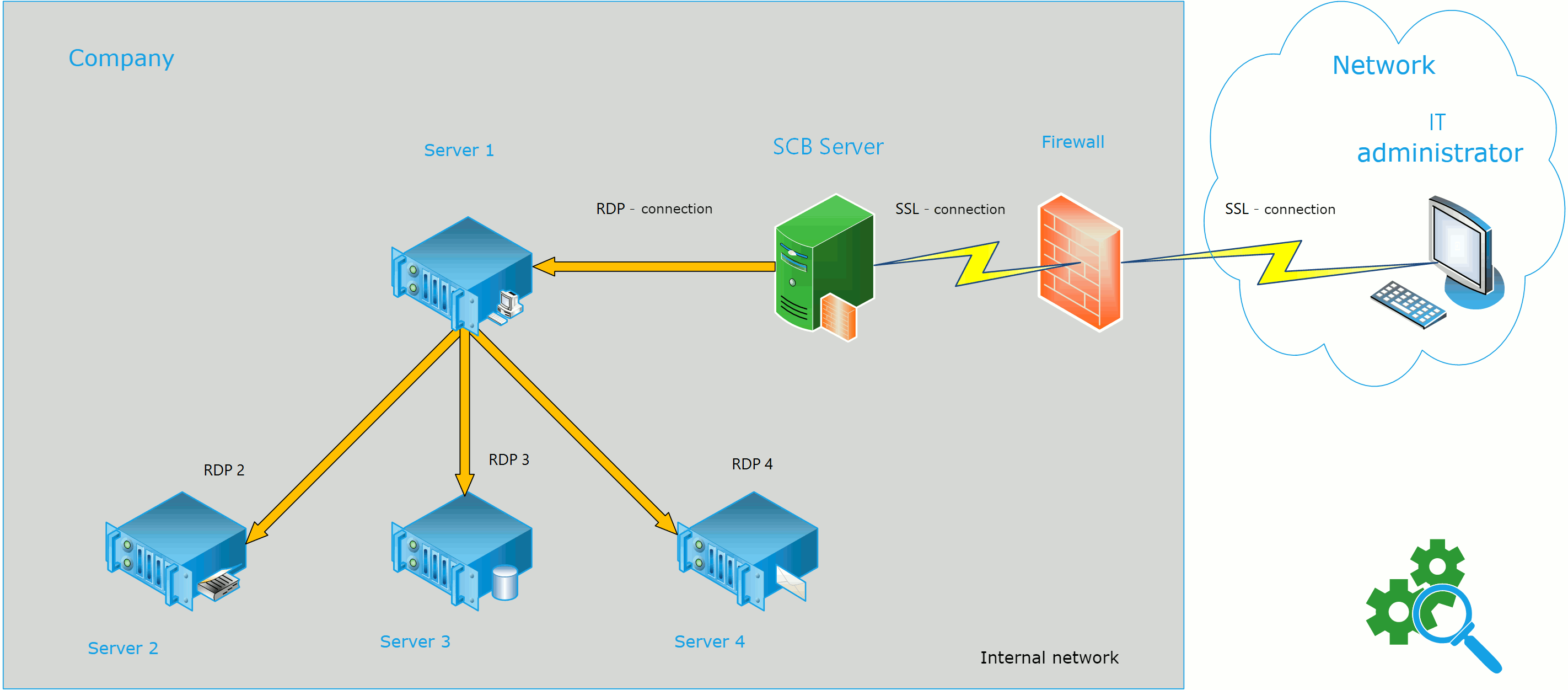
Let’s take a look at a potential plan for incorporating SCB into the company’s IT infrastructure:
(In this scenario, the company uses one server (Server 1) for SCB monitoring to decrease the number of hosts under a paid license. The admin connects to the other servers (Servers 2-4) via Server 1).
Our SCB server is configured as a remote desktop gateway. When accessing the server, the administrator authenticates on the SCB server. Upon successful authentication, an additional check is performed on the server. Next, the administrator establishes various connections to other servers, which are also monitored by the SCB server, from the controlled server.
Shell Control Box admin and control functionality are available via a web interface:
After the SCB server is configured, all traffic passing through it is automatically recorded. SCB has a single interface to view and change the configuration, reports, audit trails.
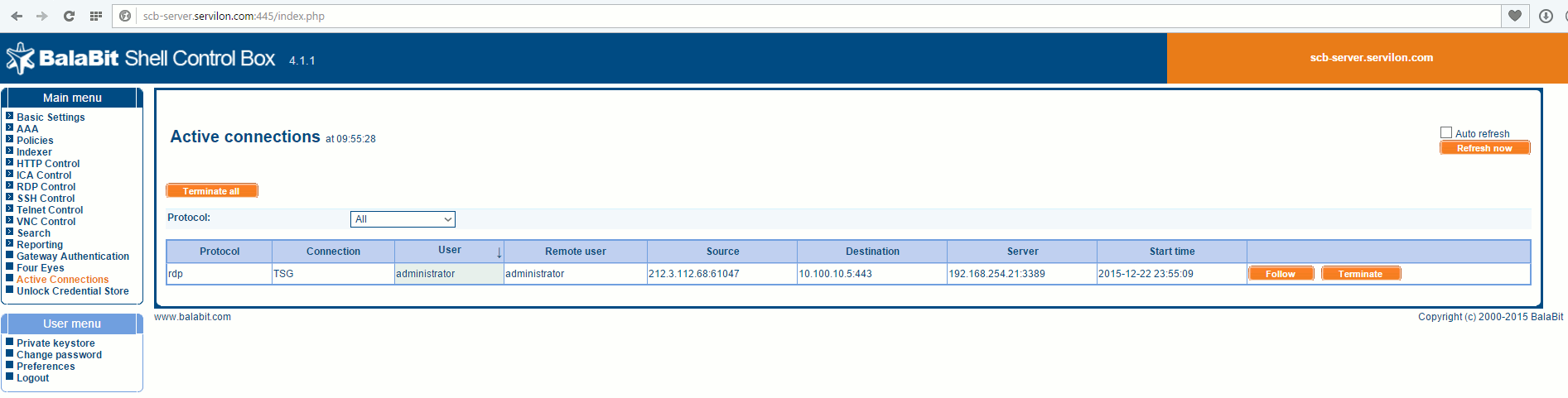
SCB provides the ability to view audits of past connections, quickly terminate current connections to servers, and observe the actions of remote administrators online.
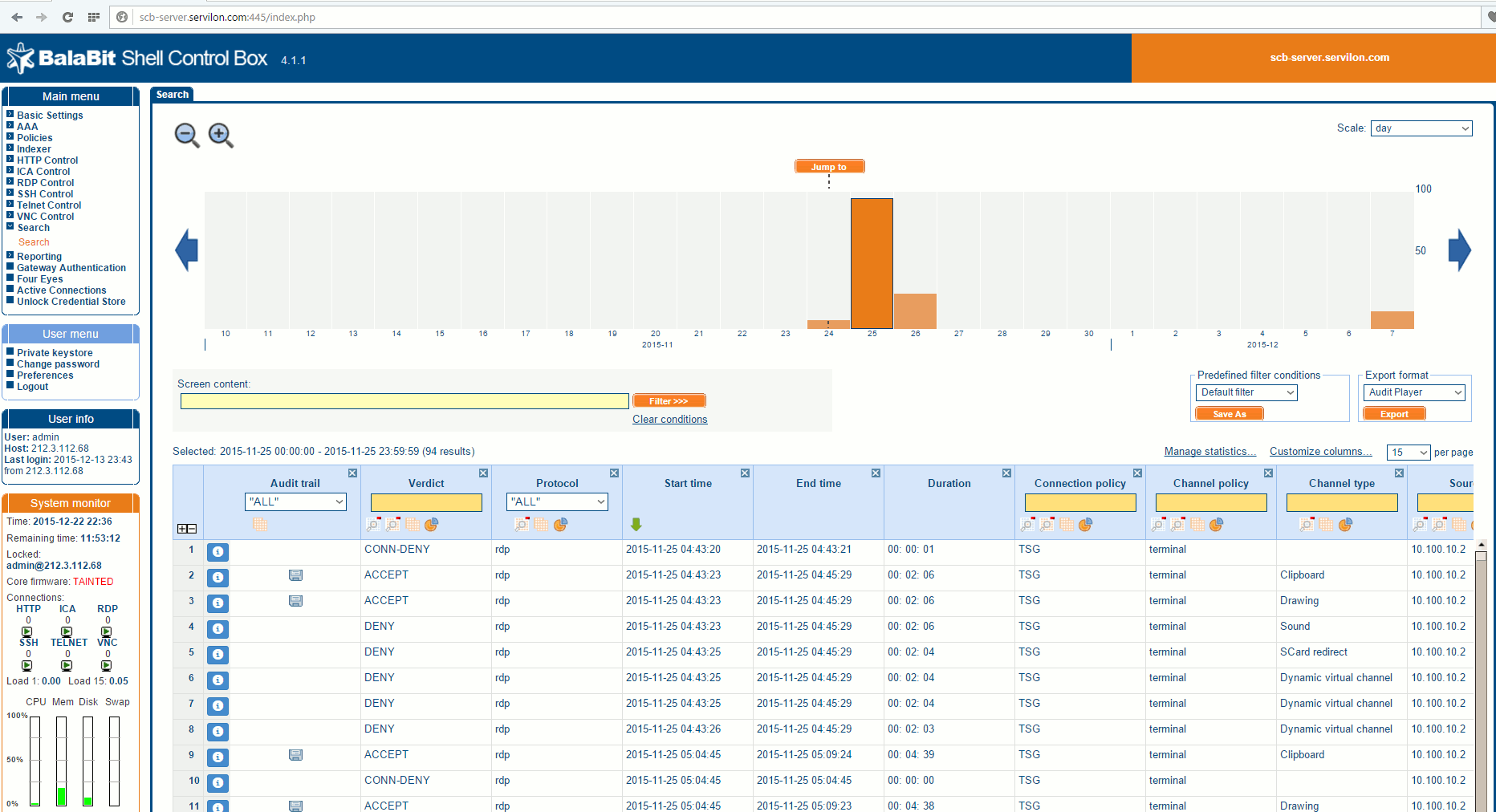
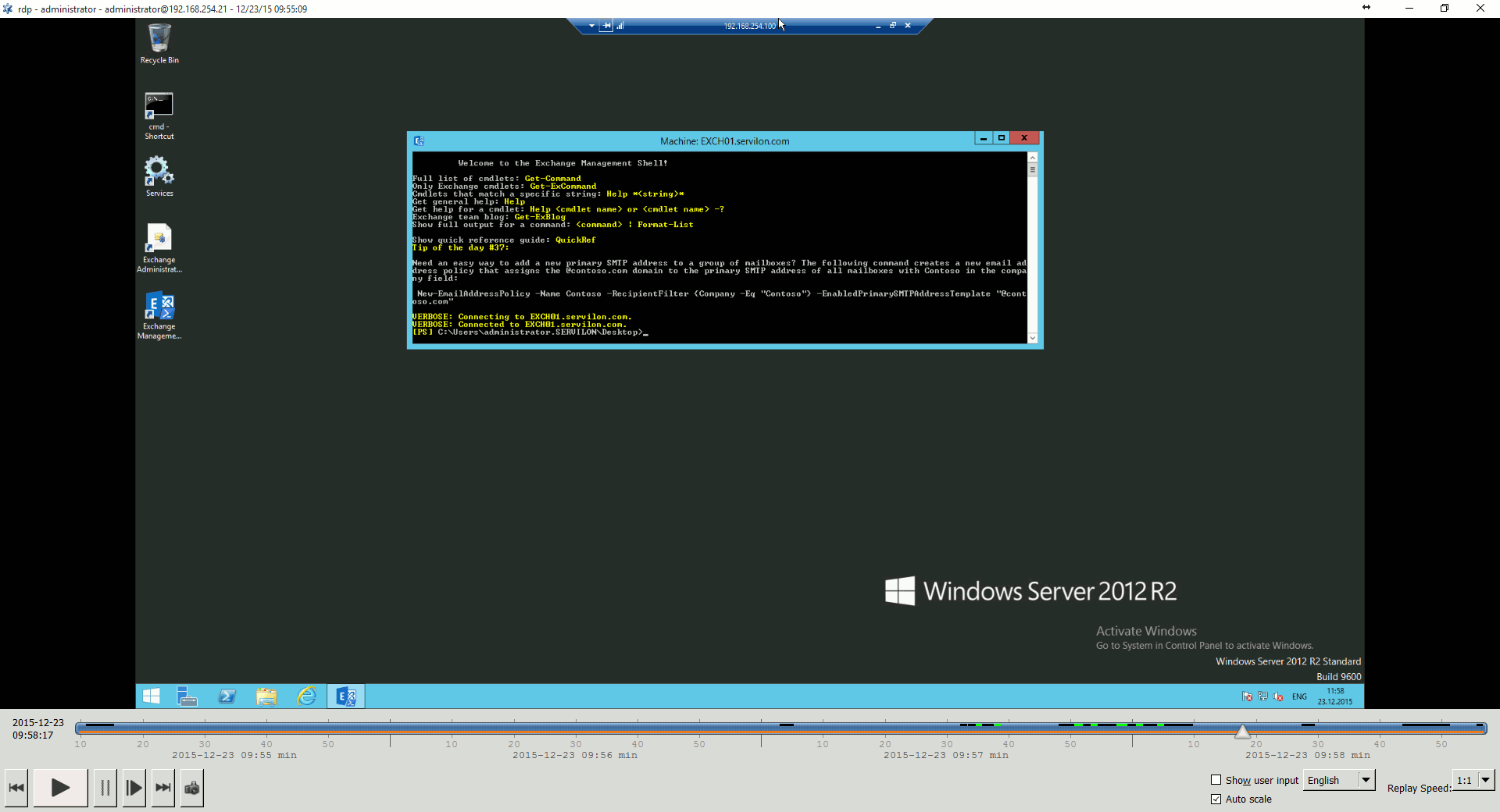
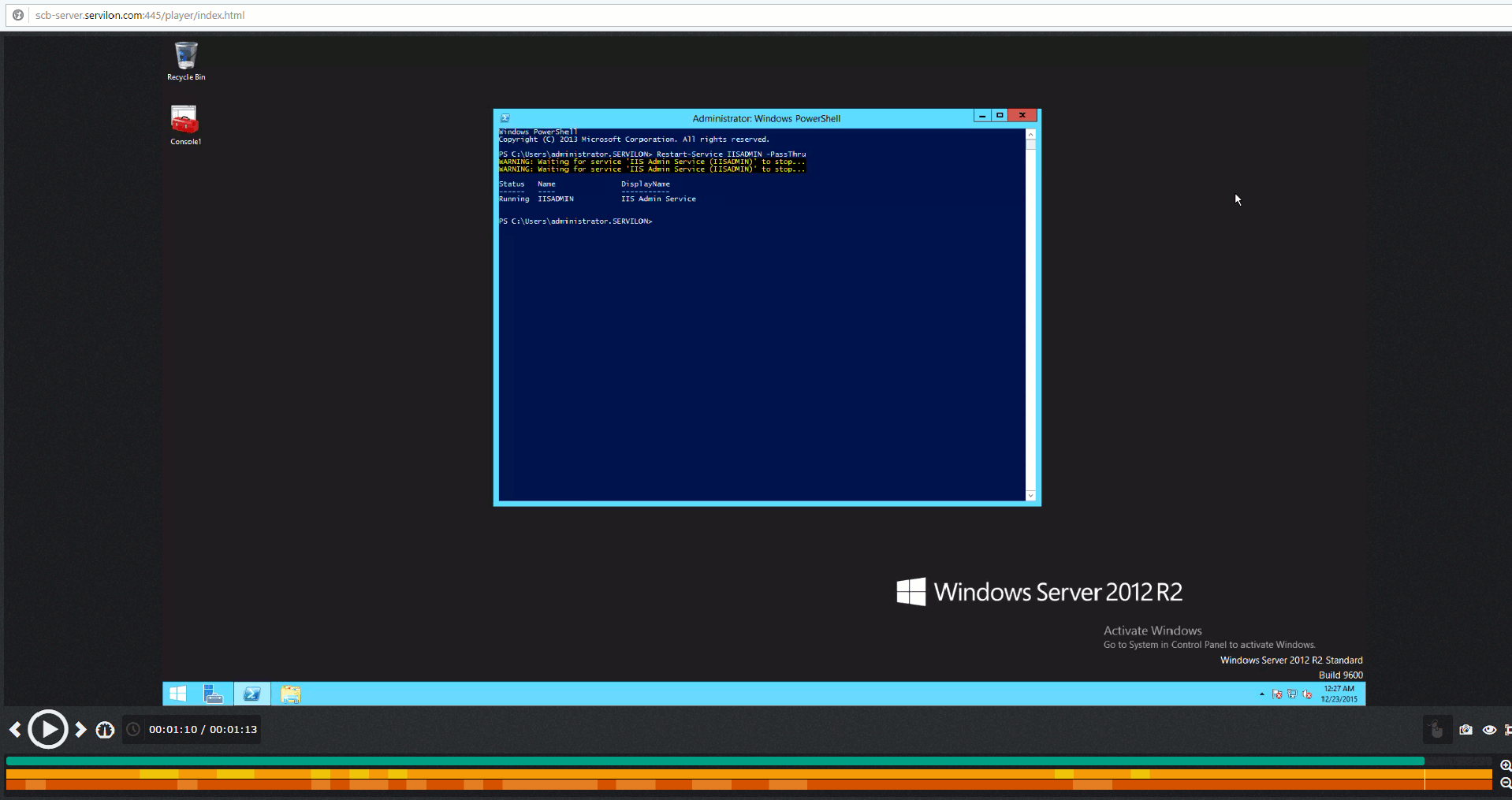
To replay audit trails, the computer has Audit Player, which allows previously saved video connections to be replayed. The screenshot below illustrates using Audit Player to replay a video from when a remote administrator performed an RDP session from a monitored server to another server in the network:
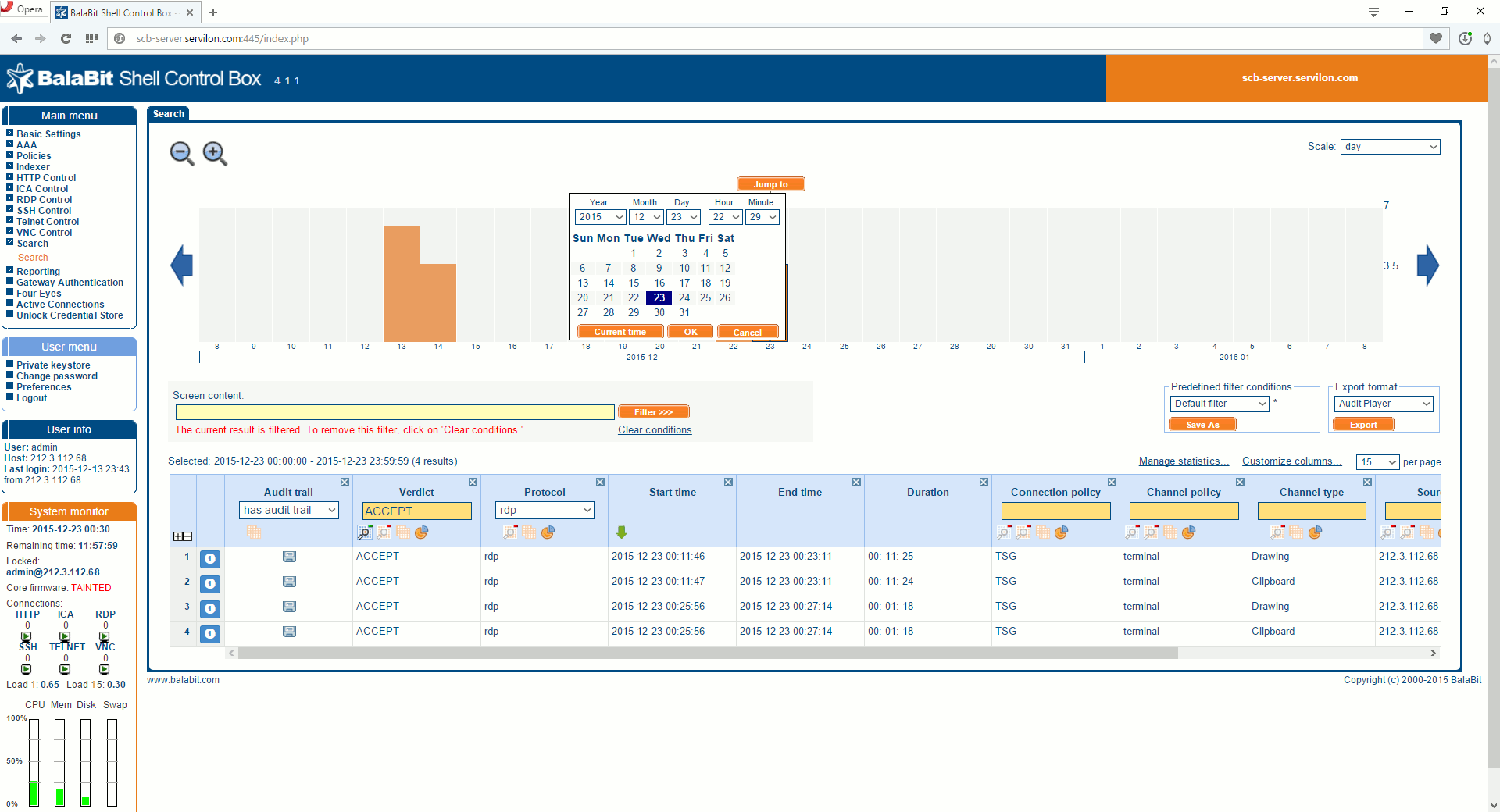
Let’s take a look at an example. Suppose a business-critical service unexpected does down on a business day. We know the time when it happened and which server is responsible for this service, so we go to the search option in the web interface. We input the date, time, type of protocol:
We need to find the corresponding session.
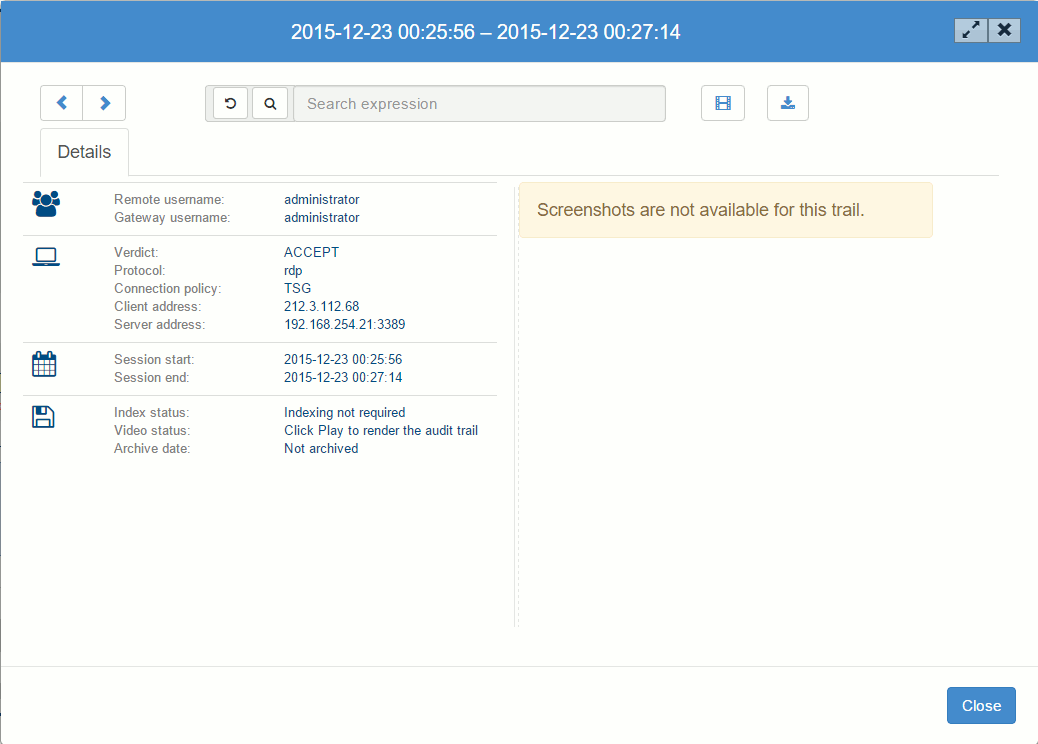
We can perform a quick replay after rendering and, if necessary, download a video of the RDP connection.
The video of the RDP connection to the server will show the work of the remote administrator who performed the unscheduled restart of the service. This audit video is great proof when resolving any claims with the IT outsourcing provider.
Conclusions
We have tried to use the functionality in BalaBit Shell Control Box to demonstrate how to create additional security that provides full control and auditing of IT companies performing server maintenance, with the ability to replay the actions performed on the servers.
Such strict auditing of IT contractors may seem to destroy trusting relationships. In fact, the situation is exactly the opposite: trust must be accompanied by transparency and the ability to verify. High-quality IT outsourcing companies should welcome such an option for client oversight, because it is a chance for the contractor to demonstrate the quality of their services and solidify the customer relationship. As an IT outsourcing company, we have a vested interest in making our customer feel safe when working with us. Moreover, we are ready to deploy such products for our customers.
As a result, we can say that the days of outsources’ uncontrolled access to customers’ IT infrastructure, and all the accompanying fears, are over. The provider’s actions can be monitored, negligence can be proved, and unauthorized actions can be tracked and prevented. The only factor is the cost, but this is largely compensated by the benefits received.
If you have any organizational or technical questions, please contact us and we will be happy to provide a consultation.