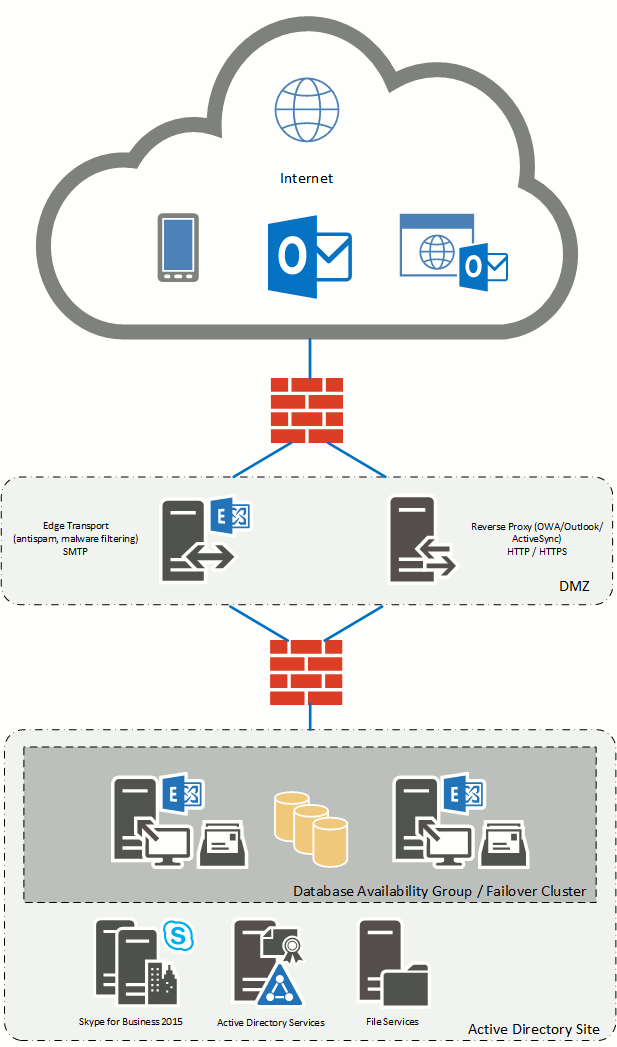
Exchange 2016 is a solution from Microsoft that provides the following business functionality:
Unified access
- Outlook Web App (OWA) offers an interface similar to Outlook’s familiar UI
- Outlook Web App (OWA) looks and works equally well in Internet Explorer, Chrome, Firefox, and Safari
- A single inbox for email, voice mail, faxes, and text messages
- You can listen to your voice mail directly in Outlook
- Users can set up a personalized automatic response system
Increased employee productivity
- Messages combined into threads
- Enhanced search system
Universal access
- Regardless of whether users are in the office, at home, on a business trip, or on the road, they will always be able to receive and send mail, schedule and accept meetings on their calendar, and view contact information for customers and coworkers
- There is no need to set up VPN connections, because all traffic is encrypted
- Outlook Voice Access (OVA) lets you use your phone to work with your mailbox. Using a PIN code and tonal commands, employees can listen to their mail, accept meeting invitations, and look up people in the address book
Mobile access
- ActiveSync technology is used to access mail from mobile devices, which allows employees to see all of their work email, contacts, calendar, and tasks directly on their mobile device
- DirectPush eliminates the need to manually check your mailbox. When a new message is received it is automatically pushed to the mobile device
- Synchronization of contacts on the mobile device with contacts on the mail server
- Employees can travel across the entire world and stay connected, receiving and responding to emails
Information security
- From the outset, Exchange has been built using the most secure means for authenticating domain users
- External access using SSL encryption
- Email encryption and signing using S/MIME technology
- Support for Information Rights Management (IRM) to protect confidential Microsoft Office documents, e.g. to prevent confidential documents from being forwarded outside the enterprise or to prevent them from being viewed or printed by persons who do not have the right to do so
- Email retention policies to prevent emails from being deleted (entirely or partially) for some period of time or based on other rules
- Message moderation by authorized employees
- Authorized employees can search for messages across all of the organization’s mailboxes when investigating incidents associated with information security
Spam protection
- This built-in basic feature can combat spam quite well
- Anti-virus scanning can take place at three levels: on edge servers (Edge Transport), on internal routing servers (HUB Transport), and database servers (Mailbox)
- Ability to integrate third-party products for more effective spam filtering
Integration of Exchange Server
This service gives you a turnkey Exchange Server integrated into your environment.
Minimum requirements:
- Active Directory;
- Exchange Server configuration (Client Access + Mailbox) – 2 x CPU / 8 GB RAM / 1 NIC / 80 GB HDD (system) + 100 GB HDD (for mailbox database, this size depends on your requirements to user mailboxes)
- Configuration of a combined edge server (reverse proxy + Edge Transport) – 4 х CPU / 8 GB RAM / 2 x NIC / 80 GB HDD (system)
Work performed during Exchange deployment:
- Installation and configuration of Windows servers;
- Preparation of the Active Directory infrastructure;
- Creation of the required DNS records and issuance of a certificate from a certificate authority;
- Installation and configuration of the Client Access and Mailbox roles;
- Installation and configuration of the Edge Transport role;
- Installation and configuration of a backup proxy server for publishing client access;
- Testing of the mail servers’ fault tolerance;
- Testing of client access from outside the organization (OWA, Outlook, ActiveSync);
- Preparation and delivery of a presentation;
- Training of IT personnel.
Additional configuration:
- Configuration of fault tolerance for the Client Access
- Publication of a certificate from trusted certification authorities
- Integration with third-party anti-spam and antivirus solutions
Estimated duration of works: approximately 2 to 5 days depending on the complexity of the configuration.