Initially, Valak malware was a threat loader but lately, it has turned into a full infostealer program and attack US and German companies. Researchers write that over half of a year Valak has received more than 20 updates. The malware spreads through phishing attacks via Microsoft Word documents with malicious macros. If the malware penetrated…
Microsoft has released the last patch for Windows 7 that broke the installing desktop wallpaper setting feature. Microsoft isn’t going to release updates for W7 anymore so users have to fix it by themselves. Updates with surprise The support period has expired on January 14, 2020 and the last update for Windows 7…
IT-monitoring is process of collecting indicators of hardware and software in the IT environment. The essence of it-monitoring is to ensure that the equipment works in the right way and on the needed level of the performance, which is required for the normal maintenance of the business. The basic monitoring solution often consists of sending…
During the life cycle of the operating system, the company provides free update support, and the end of this cycle has to come. That’s what happens to Windows 7. The strategy of Microsoft is to refuse of support Windows 7 in order to promote and popularize Windows 10 OS. They say that Windows 10 has…
The point of an update policy is to make the update process predictable, with procedures for notifying users so that they can plan their work accordingly and avoid unexpected downtime. The policy needs to address several distinct types of updates. The most familiar are the monthly cumulative security and reliability updates that are delivered on…
It would be great if the process of securing a Windows 10 device can be reduced to a simple checklist. But the process of securing is much more complicated than that. The initial setup simply establishes a security baseline. When this configuration is complete, security needs continued vigilance and ongoing effort. A big part of…
After the launch of Windows 10 the internet was flooded with messages about the collection of users’ personal data followed by multiple discussions about how to tackle the issue. The user community instantly came up with a list of major servers that collect data and tried to block them via the HOSTS file.
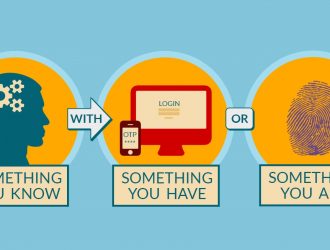
The competent approach to IT security in terms of server authorization, both inside and outside the company premises, implies a number of important measures. They include providing a unique user name and meeting password complexity requirements, as well as conducting the planned password change and non-disclosure of credentials to third parties, etc.