Nowadays, it is difficult to surprise someone by malicious advertising campaigns, but the experts of Proofpoint have discovered a new trend in this area. Now attackers are targeting not on the users ‘ browsers and in their routers. The final goal of the attacker is to inject ads into every page visited by infected victim. Interestingly, the campaign focused not on IE users, as it happens often, but for Chrome users (both desktop and mobile versions).
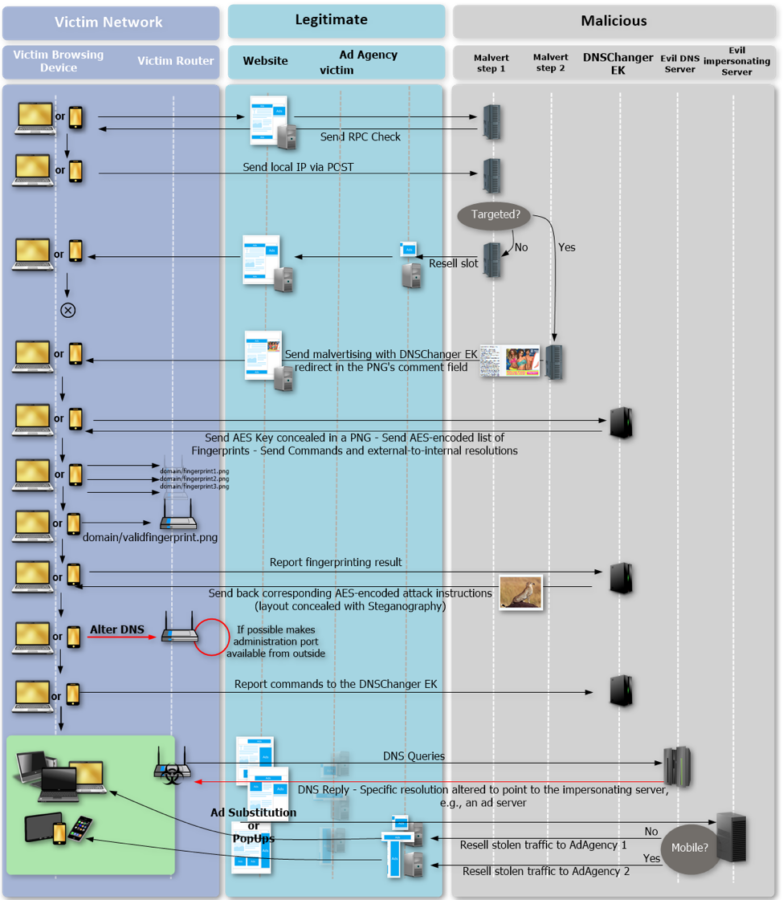
Attack scheme
Hackers do in the following way: on legitimate sites buy advertising space for ad placement. For this the attackers use AdSupply ad network, OutBrain, Popcash, Propellerads and Taboola. In the ad embedded malicious JavaScript code that uses WebRTC request to Mozilla’s STUN server to discover the local IP address of the victim. Based on this information, the malware determines by a local network user in any home router. If the answer is positive, the attack continues. If not, the user shows an ordinary, harmless advertising, and he avoids trouble.
The owners of the routers do not show a harmless ad. Advertising will take them straight to the exploit kit DNSChanger, which continues the attack. Using steganography, the attacker sends router of the victim image, which contains the AES key. Malicious advertising uses this key to decrypt further traffic received from DNSChanger. So attackers hide their operations from the attention of is professionals.
After receiving AES key, DNSChanger sends the victim a list of the distinguishing features of 166 router (including various models of Linksys, Netgear, D-Link, Comtrend, Zyxel, and Pirelli), which is set based on the type of router, which is then transmitted to the attackers control server. The server has a list of vulnerabilities and hard-coded credentials from different devices, which are used to intercept control over the victim’s router. Proofpoint experts noted that in some cases (if the model allows), the attackers are trying to create an external connection to an administrative port on the router and take control directly.
